Cloud Infrastructure & Service Management Part-2
Cloud Infrastructure and Deep Architecture
LINK PART 1 : > Cloud Infrastructure and Deep Architecture
PART - 2 Cloud Service Management
- Cloud Service Lifecycle
- Service Level Agreements (SLAs) in Cloud
- Cloud Governance and Compliance
- Billing and Cost Management in Cloud
- Cloud Monitoring and Analytics
- Resource Provisioning and Management
- Automation in Cloud Service Management
- Incident Management in Cloud
- Identity and Access Management (IAM)
- Cloud Vendor Management
- Cloud Migration Strategies
- Backup and Restore in Cloud
- Performance Optimization of Cloud Services
- Multi-Cloud and Hybrid Cloud Management
Microservices Architecture/ CICD,GDPR
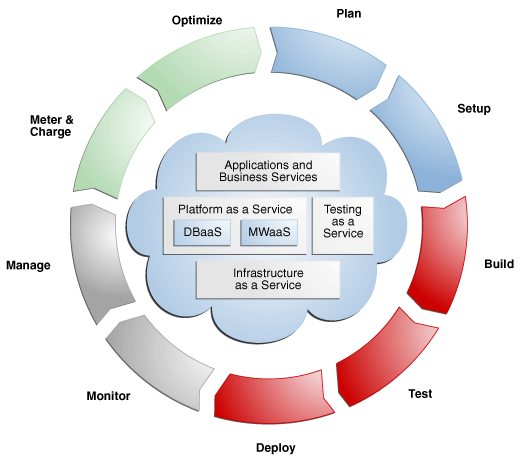
1. Cloud Service Lifecycle
LINK : Cloud Service ,
Service Life Cycle Management
Cloud Service Lifecycle
The Cloud Service Lifecycle consists of structured phases that ensure effective management of cloud services from inception to retirement. The phases are:
1. Planning
- Identifying business requirements.
- Feasibility analysis for adopting cloud services.
- Service design, including architecture and compliance considerations.
2. Deployment
- Implementation and configuration of cloud services.
- Ensuring services are operational and integrated with existing systems.
- Testing for functionality, scalability, and security.
3. Operation
- Day-to-day management of cloud services, including monitoring, scaling, and incident resolution.
- Performance optimization to meet Service Level Agreements (SLAs).
- Implementing updates and patches as necessary.
4. Optimization
- Fine-tuning resources for cost efficiency.
- Analyzing usage patterns to enhance service performance.
- Leveraging analytics for proactive issue resolution.
5. Retirement
- Decommissioning outdated or redundant services.
- Migrating data to new systems or archiving as needed.
- Ensuring compliance with data retention and destruction policies.
Key Considerations for Exams
- SLAs: Focus on how SLAs impact each phase.
- Automation: Understand how automation tools streamline lifecycle management.
- Governance: Know the role of governance frameworks in managing the lifecycle.
- Cost Management: Be prepared to explain cost control in lifecycle stages.
2 Service Level Agreements (SLAs)
in Cloud
Link : (SLAs)
A Service Level Agreement (SLA) is a contract between a cloud provider and a customer that defines the level of service, including uptime, performance, and support.
Key Elements:
- Availability: Uptime guarantees (e.g., 99.9%).
- Performance: Response time and throughput.
- Support: Response and resolution times for issues.
- Security: Data protection and compliance.
- Penalties: Compensation if SLAs aren't met.
Types of SLAs:
- Customer-to-Cloud Service Provider SLA: This is the agreement between the cloud service provider and the customer. It specifies performance, security, support, and availability requirements.
- Internal SLA: These SLAs are internal agreements within an organization to ensure service quality between teams (e.g., between IT and operations).
- Multi-tier SLAs: These are layered SLAs with different service levels depending on the customer's requirements. For example, a basic service may offer 99.5% uptime, while a premium service may offer 99.99%.
Automation in Cloud
Automation in cloud computing refers to the use of tools to manage cloud services without manual intervention.
Benefits:
- Cost Efficiency: Reduces operational costs.
- Scalability: Automatically scales resources.
- Speed: Speeds up deployment and issue resolution.
Types of Cloud Automation
1 Infrastructure Automation:
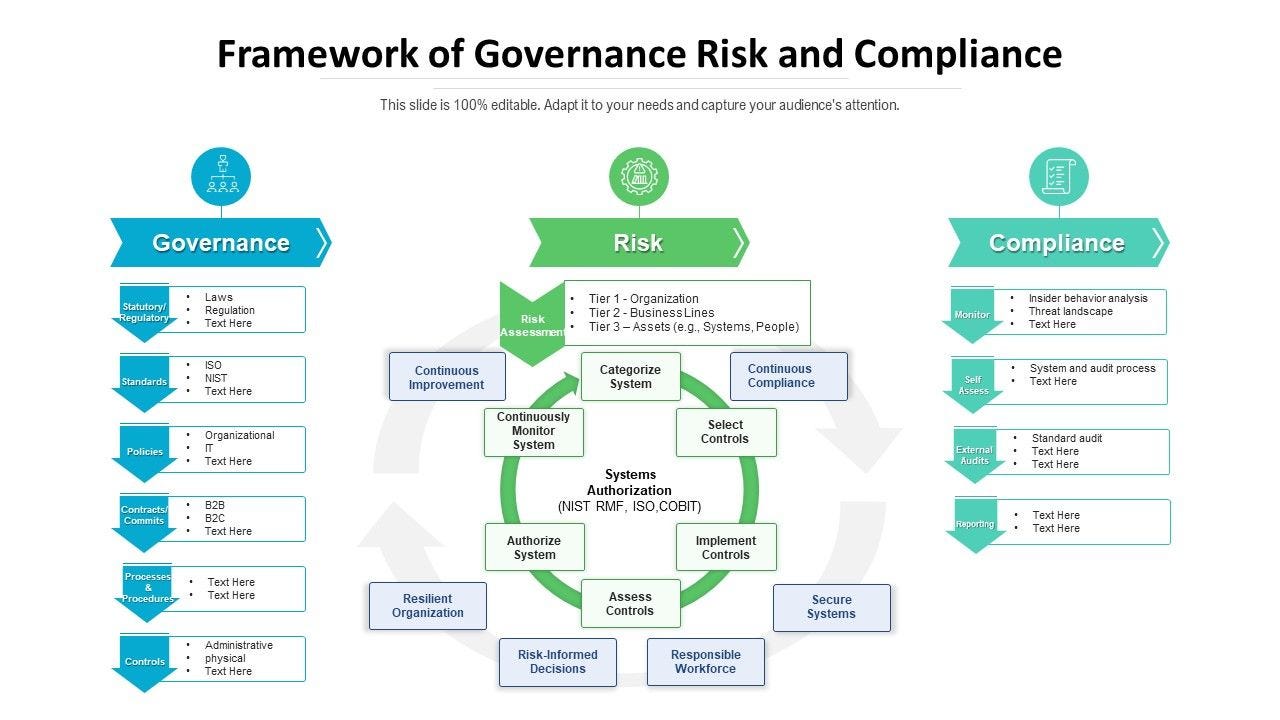
Cloud Governance refers to the processes, policies, and controls that ensure cloud services are used in a responsible, effective, and secure manner. It encompasses the strategic, financial, operational, and compliance aspects of managing cloud resources.
Cloud Compliance focuses on adhering to external regulations, industry standards, and internal policies to ensure that the use of cloud services meets legal, security, and privacy requirements.
Key Concepts to Understand for Exams:
Cloud Governance Framework:
- Defines policies for managing cloud resources.
- Ensures alignment with business objectives and regulatory requirements.
- Key components include security, cost management, and service performance.
Compliance Requirements:
- Legal and regulatory standards (e.g., GDPR, HIPAA, SOC 2).
- Industry standards like ISO 27001 (Information Security), PCI-DSS (Payment Card Industry), and FedRAMP (Federal Risk and Authorization Management Program).
- Local data residency requirements for data storage and processing.
Governance Models:
- Centralized: One team manages governance policies across all departments.
- Decentralized: Each department or business unit manages their own governance policies.
- Hybrid: A combination of centralized and decentralized approaches.
Cloud Security and Risk Management:
- Involves managing cloud security risks, including data protection, access control, and vulnerability management.
- Identity and Access Management (IAM) is crucial for controlling access to cloud resources.
- Data Encryption: Protecting sensitive data through encryption both at rest and in transit.
Cloud Compliance Tools and Solutions:
- Cloud Security Posture Management (CSPM): Ensures that cloud services are configured securely.
- Compliance Automation Tools: Tools like AWS Config, Azure Policy, and Google Cloud Security Command Center help automate compliance checks.
- Audit Trails and Monitoring: Ensures all activities are logged for accountability and regulatory audits.
Cost Governance and Management:
- Managing cloud spending by setting budgets, monitoring usage, and applying cost-control mechanisms (e.g., Reserved Instances, Auto-scaling).
- Use of Cost Management tools like AWS Cost Explorer, Azure Cost Management, and Google Cloud Billing.
Important Topics for Exam Preparation:
- Risk Assessment: How to assess and mitigate risks in cloud environments.
- Data Protection: Ensuring data privacy and integrity.
- Service Level Agreements (SLAs): Understanding how SLAs relate to governance and compliance.
- Cloud Vendor Management: Ensuring third-party vendors adhere to compliance standards.
- Auditing and Reporting: Mechanisms for auditing cloud environments and generating reports for compliance.
4 Billing and Cost Management in Cloud
Link : BIlling & Cost cloud


Cloud Billing Basics:
- Pay-as-you-go: Pay for usage.
- Reserved Instances: Pre-pay for discounts.
- Spot Instances: Use unused capacity at lower cost.
- Free Tier: Limited free usage for testing.
Cost Management Strategies:
- Budgeting: Set limits using tools (AWS Budgets, Azure Cost Management).
- Resource Tagging: Track costs by tags (e.g., department, project).
- Auto-scaling: Adjust resources automatically to reduce costs.
Cost Optimization:
- Right-Sizing: Select correct instance types.
- Elasticity: Scale resources based on demand.
- Idle Resource Management: Remove unused resources.
- Savings Plans: Pre-commit to reduce costs.
Billing Tools:
- AWS: AWS Cost Explorer, Billing Dashboard.
- Azure: Azure Cost Management and Billing.
- Google Cloud: Cloud Billing Reports.
Multi-Cloud Cost Management:
- Use third-party tools (CloudHealth, Flexera) for multi-cloud cost control.
Chargeback vs Showback:
- Chargeback: Allocate costs to departments.
- Showback: Display costs without charging.
Monitoring and Alerts:
- Set cost alerts for budget thresholds and monitor spending in real-time.
5 Cloud Monitoring and Analytics
Link : Cloud Monitoring and Analytics

Cloud Monitoring and Analytics
Cloud Monitoring and Analytics refer to the processes and tools used to monitor, measure, and analyze the performance, health, and usage of cloud services and resources. It plays a vital role in ensuring system reliability, efficiency, and cost-effectiveness.
Key Concepts for Exam Preparation:
Cloud Monitoring:
- Definition: Continuous observation of cloud resources and services for performance, availability, and health.
- Key Metrics: CPU usage, memory, network traffic, storage, response time, error rates.
- Alerts: Notifications based on threshold violations (e.g., high CPU usage or service downtime).
Cloud Analytics:
- Definition: The process of analyzing cloud service data to gain insights into performance, usage trends, and operational efficiencies.
- Use Cases: Identifying bottlenecks, optimizing costs, improving resource allocation, enhancing security.
Cloud Monitoring Tools:
AWS CloudWatch:
- Monitors AWS cloud resources (EC2, S3, RDS, etc.).
- Provides metrics, logs, and alarms for performance tracking.
- CloudWatch Logs: Track logs from various services.
Azure Monitor:
- Monitors Azure resources (VMs, databases, etc.).
- Provides metrics, logs, and dashboards.
- Application Insights: Real-time app performance monitoring.
Google Cloud Monitoring:
- Monitors Google Cloud resources and applications.
- Provides detailed insights into application performance.
- Stackdriver: Integrates monitoring and logging.
Analytics in Cloud:
Data Analytics Tools:
- AWS: AWS QuickSight for business intelligence, and AWS Athena for querying S3 data.
- Azure: Azure Synapse Analytics and Azure Data Explorer for big data analytics.
- Google Cloud: BigQuery for large-scale data analytics and data visualization.
Log Analytics:
- Collecting and analyzing logs to identify trends, diagnose problems, and improve services.
- Tools: ELK Stack (Elasticsearch, Logstash, Kibana), Splunk, Datadog.
Benefits of Cloud Monitoring and Analytics:
- Improved Performance: Optimize resource usage and application performance.
- Cost Optimization: Monitor resource usage to avoid over-provisioning and reduce costs.
- Security: Detect suspicious activities, anomalies, and potential security threats.
- Availability: Ensure high availability by detecting failures and triggering automatic remediation.
Exam Tips:
- Understand how cloud monitoring and analytics tools work in major cloud platforms (AWS, Azure, Google Cloud).
- Be able to explain how data can be collected, analyzed, and used for decision-making.
- Familiarize yourself with common monitoring metrics and alert thresholds.
6 Resource Provisioning and Management
Link : Resource Provisioning and Management


Resource Provisioning and Management
Resource Provisioning involves allocating cloud resources like compute, storage, and network to meet application needs. Resource Management ensures efficient and continuous monitoring, scaling, and optimization of these resources.
Key Concepts for Exam Preparation
Types of Provisioning:
- Manual Provisioning: Admin manually allocates resources (slow, error-prone).
- Automated Provisioning: Uses tools/scripts to provision resources (e.g., Terraform, AWS CloudFormation).
- Self-Service Provisioning: Users request resources directly via portals.
Resource Management:
- Monitoring: Track usage, health, and performance.
- Scaling:
- Vertical Scaling: Increase/decrease resource size (e.g., CPU, memory).
- Horizontal Scaling: Add/remove instances.
- Optimization: Identify and eliminate underutilized resources.
Provisioning Models:
- On-Demand: Allocate resources as needed (flexible, higher cost).
- Reserved: Pre-allocate resources at a discount.
- Spot Instances: Use spare capacity at lower cost.
Key Tools by Providers:
- AWS: CloudFormation, EC2 Auto Scaling, Elastic Beanstalk.
- Azure: Resource Manager (ARM), Virtual Machine Scale Sets.
- Google Cloud: Deployment Manager, Compute Engine Autoscaler.
Infrastructure as Code (IaC):
- Automates resource provisioning using code (e.g., Terraform, Ansible).
- Enables version control and repeatable deployments.
Cost Control:
- Use budgets and quotas to limit resource usage.
- Identify idle or over-provisioned resources.
Benefits:
- Agility: Quickly scale resources to meet demands.
- Cost Efficiency: Pay only for what you use, avoid over-provisioning.
- Reliability: Ensures resource availability with automated scaling.
Exam Tips:
- Understand IaC concepts and its tools (e.g., Terraform, CloudFormation).
- Be prepared to explain scaling techniques and cost management strategies.
- Focus on the role of automated tools in provisioning and management.
7 Automation in Cloud Service Management
Link : TECH

Automation in Cloud Service Management
Automation in Cloud Service Management refers to the use of tools and scripts to manage cloud resources and services without manual intervention, ensuring efficiency, consistency, and scalability.
Key Concepts for Exam Preparation
Types of Automation:
- Infrastructure Automation: Automates provisioning and configuration (e.g., Terraform, AWS CloudFormation).
- Application Deployment: Automates app deployment via CI/CD pipelines (e.g., Jenkins, GitLab CI).
- Resource Scaling: Automatically adjusts resources based on demand (e.g., AWS Auto Scaling, Azure VM Scale Sets).
- Monitoring and Alerts: Automates health checks and triggers alerts (e.g., AWS CloudWatch, Azure Monitor).
- Security Automation: Automates vulnerability scans and access control (e.g., IAM rules, automated backups).
Benefits of Automation:
- Efficiency: Reduces manual efforts in resource provisioning and management.
- Consistency: Ensures uniform configurations across environments.
- Scalability: Enables dynamic scaling based on workload.
- Cost Optimization: Prevents over-provisioning with real-time resource adjustments.
Key Tools:
- AWS: CloudFormation, Lambda, Auto Scaling.
- Azure: Azure Automation, Azure Logic Apps.
- Google Cloud: Deployment Manager, Cloud Functions.
- Cross-Platform: Ansible, Puppet, Chef.
Exam Tips:
- Understand the role of Infrastructure as Code (IaC) in automating cloud management.
- Be prepared to explain CI/CD pipelines and their impact on app delivery.
- Familiarize yourself with automated scaling, monitoring, and cost control strategies.
8 Incident Management in Cloud
Link : Incident Management in Cloud
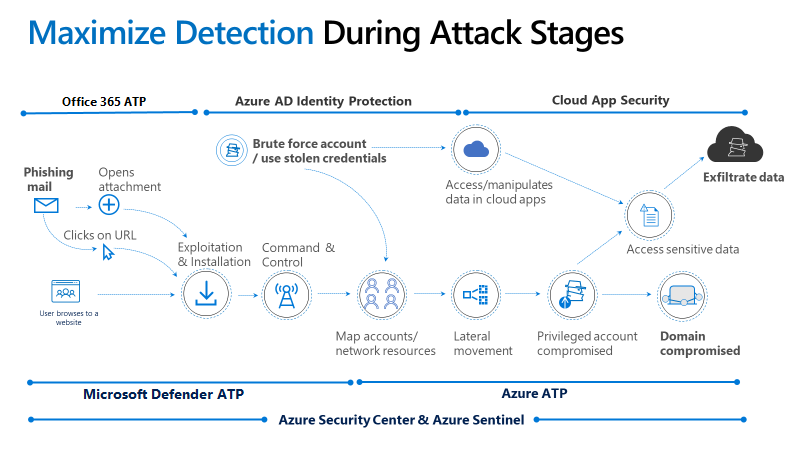
DATA RESPONCE MNAGEMENT
Incident Management in Cloud refers to the processes and tools used to detect, respond to, and resolve unplanned disruptions or service degradations in cloud environments.
Key Concepts
Incident Management Lifecycle:
- Detection: Identify incidents through monitoring tools (e.g., CloudWatch, Azure Monitor).
- Response: Acknowledge and prioritize incidents based on severity (P1, P2, etc.).
- Resolution: Resolve issues using root cause analysis and corrective actions.
- Recovery: Restore services and verify functionality.
- Post-Incident Review: Analyze incidents to prevent future occurrences.
Types of Cloud Incidents:
- Service Downtime: Unavailability of cloud resources.
- Security Breaches: Unauthorized access or data breaches.
- Performance Issues: High latency, resource bottlenecks.
- Configuration Errors: Misconfigured settings causing failures.
Incident Response Strategies:
- Automated Detection: Use tools to identify anomalies (e.g., AWS CloudTrail, Splunk).
- Escalation: Notify appropriate teams for faster resolution.
- Disaster Recovery: Activate backup and recovery plans during critical failures.
Incident Management Tools:
- AWS: AWS CloudWatch, CloudTrail, Systems Manager.
- Azure: Azure Monitor, Service Health, Log Analytics.
- Google Cloud: Cloud Monitoring, Incident Response Management.
- Third-Party Tools: PagerDuty, ServiceNow, Opsgenie.
Best Practices:
- Automate Monitoring: Use AI/ML for predictive issue detection.
- Define SLAs and Priorities: Ensure quick response times for critical incidents.
- Conduct Simulations: Test incident response plans (e.g., Chaos Engineering).
- Documentation: Maintain detailed incident logs for audits and learning.
9 Identity and Access Management (IAM)
Link : IAM
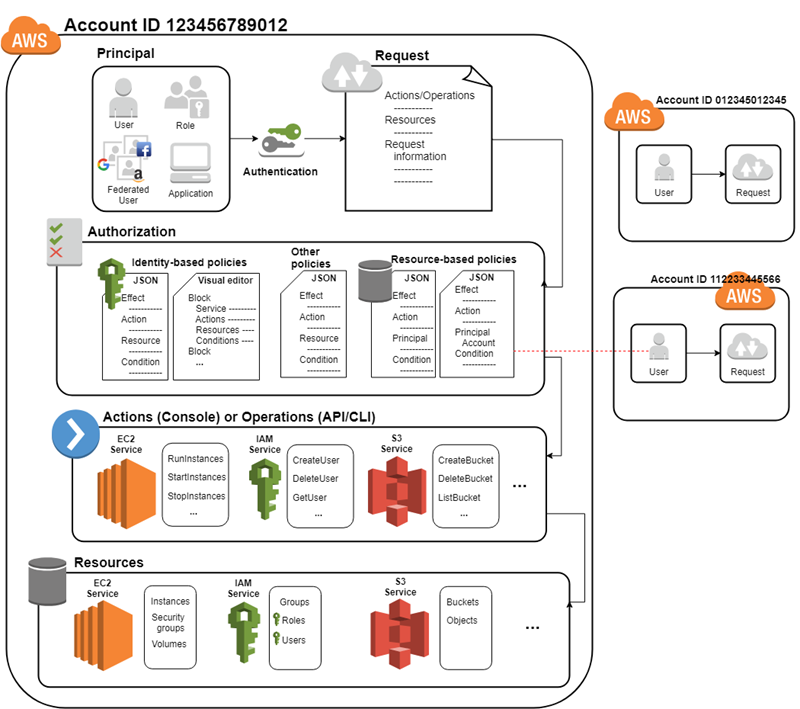
Key Concepts for Exam Preparation
IAM Basics:
- Users: Individual identities (e.g., employees, applications).
- Groups: Collections of users with common permissions.
- Roles: Sets of permissions granted to users or groups.
- Policies: Documents that define permissions (e.g., allow, deny).
Authentication vs Authorization:
- Authentication: Verifying the identity of a user (e.g., passwords, MFA).
- Authorization: Determining what actions an authenticated user can perform (e.g., read, write).
IAM Components:
- Users & Roles: Create and manage user accounts and assign roles.
- MFA (Multi-Factor Authentication): Adds an extra layer of security.
- Temporary Security Credentials: Short-lived credentials for specific tasks (e.g., AWS STS).
- Service Accounts: For automated processes (e.g., cloud applications).
IAM Best Practices:
- Least Privilege Access: Grant only the minimum permissions needed.
- Role-Based Access Control (RBAC): Assign permissions based on job functions.
- MFA Enforcement: Require multi-factor authentication for sensitive actions.
- Regular Auditing: Continuously review and update IAM policies.
IAM Tools by Providers:
- AWS: IAM, AWS SSO, AWS Organizations.
- Azure: Azure Active Directory (AAD), RBAC.
- Google Cloud: Cloud IAM, Identity-Aware Proxy (IAP).
Types of Identity and Access Management (IAM) in Cloud
User-Based Access:
- Individual user identities (e.g., employees or service accounts) are created and managed.
- Permissions are assigned directly to users.
Group-Based Access:
- Groups are created with a set of permissions.
- Users are added to groups, inheriting the group’s permissions.
Role-Based Access Control (RBAC):
- Permissions are assigned based on roles rather than individual users.
- Roles are mapped to job functions (e.g., admin, user, developer).
Attribute-Based Access Control (ABAC):
- Access decisions are based on attributes (e.g., department, project).
- Policies are created using attributes like environment, resource type, etc.
Federated Identity Management:
- Allows users from external sources (e.g., social media, enterprise directories) to access cloud resources.
- Uses identity providers (e.g., SSO, OAuth, SAML).
Temporary Access:
- Provides short-term access (e.g., AWS STS, Google Cloud Temporary Credentials) for specific tasks.
Multi-Factor Authentication (MFA):
- Requires two or more authentication factors (e.g., password + OTP) for access to sensitive resources.
Exam Tips:
- Understand IAM concepts (users, roles, policies) and how to implement them.
- Be prepared to explain MFA and least privilege principles.
- Know IAM tools and their functions across major cloud platforms.
10 Cloud Vendor Management
Link : VENDEOR CLOUD
Cloud Vendor Management (For Top Exams)
Cloud Vendor Management involves selecting, managing, and maintaining relationships with cloud service providers to ensure optimal performance, cost efficiency, and compliance.
Key Concepts for Exam Preparation
Vendor Selection Criteria:
- Service Level Agreements (SLAs): Ensure providers meet performance and uptime guarantees.
- Cost: Analyze pricing models (pay-as-you-go, reserved instances, etc.).
- Security and Compliance: Assess the provider’s security protocols and regulatory compliance (e.g., GDPR, HIPAA).
- Scalability and Flexibility: Ensure the provider can scale resources as needed.
- Support: Evaluate the level of customer support and availability.
Vendor Risk Management:
- Vendor Lock-in: Minimize dependency on a single provider by evaluating portability and interoperability.
- Business Continuity: Ensure the provider has disaster recovery plans and redundancy.
- Data Sovereignty: Understand where data is stored and how it complies with legal/regulatory requirements.
Multi-Cloud and Hybrid Cloud:
- Multi-Cloud: Use services from multiple cloud vendors to avoid vendor lock-in and increase resilience.
- Hybrid Cloud: Integrate on-premises infrastructure with cloud resources for greater flexibility.
Contract Negotiation and Management:
- SLAs and Penalties: Define clear SLAs, performance benchmarks, and penalties for non-compliance.
- Termination Clauses: Include exit strategies and data retrieval procedures if ending the relationship.
- Pricing Terms: Negotiate clear pricing, billing models, and cost controls.
Vendor Performance Monitoring:
- KPIs (Key Performance Indicators): Set metrics for uptime, performance, and response times.
- Regular Audits: Perform periodic reviews of vendor performance and security compliance.
Vendor Relationship Management:
- Collaboration: Work closely with vendors for mutual growth, issue resolution, and innovation.
- Continuous Improvement: Regularly review vendor performance and explore opportunities for optimization.
11 Cloud Migration Strategies
Link : Cloud Migration
Cloud Migration Strategies
Cloud Migration Strategies refer to the approaches and methods used to move data, applications, and workloads from on-premises or other cloud environments to a cloud platform.
Key Concepts for Exam Preparation
Migration Strategies (The 6 R's):
- Rehost (Lift and Shift): Move applications as-is to the cloud without modification.
- Replatform: Move applications with minor changes to optimize for the cloud.
- Repurchase: Replace legacy systems with cloud-native applications (e.g., SaaS).
- Refactor/Re-architect: Redesign applications to fully leverage cloud capabilities.
- Retire: Decommission outdated or unnecessary systems.
- Retain: Keep certain applications on-premises if they’re critical or don’t fit cloud environments.
Phases of Cloud Migration:
- Assessment: Analyze current infrastructure and determine cloud suitability.
- Planning: Create a detailed migration plan with timelines, resource allocation, and risk management.
- Execution: Migrate workloads and data in phases to ensure minimal disruption.
- Optimization: Post-migration, optimize for cost, performance, and security.
Tools and Services for Migration:
- AWS: AWS Migration Hub, AWS Database Migration Service, Server Migration Service.
- Azure: Azure Migrate, Azure Site Recovery.
- Google Cloud: Migrate for Compute Engine, Database Migration Service.
Challenges in Cloud Migration:
- Downtime: Ensuring minimal service interruptions during migration.
- Data Security: Protecting data integrity and privacy during the transfer.
- Cost Overruns: Monitoring cloud costs during migration and after go-live.
- Compatibility Issues: Ensuring applications and data integrate seamlessly in the cloud.
Hybrid and Multi-Cloud Migration:
- Hybrid Cloud Migration: Moving workloads between on-premises and cloud environments.
- Multi-Cloud Migration: Distributing workloads across multiple cloud providers to avoid vendor lock-in.
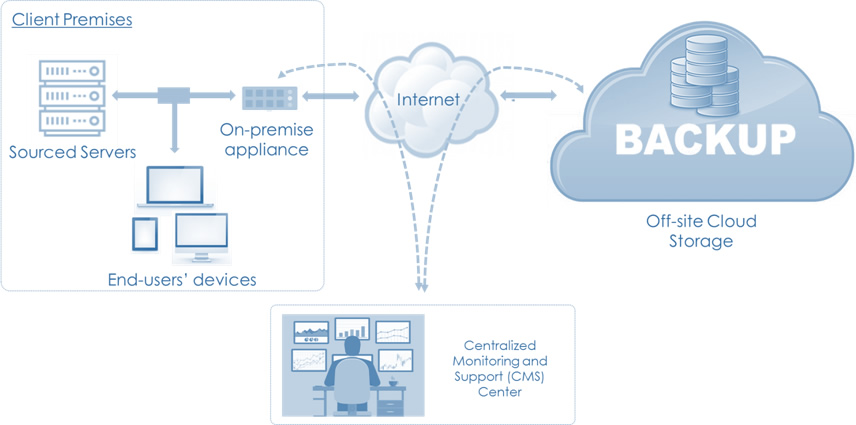
12 Backup and Restore in Cloud
Link : Backup and Restore

Backup and Restore in Cloud
Cloud Backup ensures data protection and availability, while Restore allows recovery in case of loss or failure.
Key Backup Types:
Full Backup: Backs up all data.
- Pro: Comprehensive.
- Con: Time and storage-intensive.
Incremental Backup: Backs up only changes since the last backup.
- Pro: Faster, storage-efficient.
- Con: Requires all previous backups for restore.
Differential Backup: Backs up changes since the last full backup.
- Pro: Faster restore than incremental.
- Con: Larger than incremental.
Continuous Data Protection (CDP): Real-time backup.
- Pro: Near-zero data loss.
- Con: High storage usage.
Cloud Backup Models:
- Manual Backups: User-initiated backups.
- Automated Backups: Scheduled, consistent backups.
Restore Strategies:
- Full Restore: Restores all data.
- Partial Restore: Restores specific data.
- Granular Restore: Restores individual items like files or database entries.
Best Practices:
- Automate backups.
- Encrypt backup data.
- Test restore processes regularly.
- Use georedundant storage for disaster recovery.
13 Performance Optimization of Cloud Services
Link : Cloud
Performance Optimization in cloud services involves improving the speed, efficiency, and scalability of cloud-based applications and resources.
Key Strategies for Optimization:
Right-Sizing Resources:
- Adjust compute, storage, and network resources to match application needs, avoiding over-provisioning.
Auto-Scaling:
- Automatically scale resources up or down based on demand to ensure optimal performance and cost-efficiency.
Caching:
- Use caching mechanisms (e.g., CloudFront, Redis) to store frequently accessed data and reduce latency.
Load Balancing:
- Distribute traffic across multiple servers to ensure high availability and prevent bottlenecks.
Content Delivery Networks (CDNs):
- Use CDNs to deliver content quickly to users by caching data closer to end-users globally (e.g., AWS CloudFront, Azure CDN).
Optimizing Storage:
- Use the right storage types (e.g., SSD for high-speed needs, object storage for scalability) to balance speed and cost.
Monitoring and Analytics:
- Regularly monitor performance metrics (e.g., latency, throughput) to identify and resolve performance issues.
Serverless Architecture:
- Use serverless services (e.g., AWS Lambda, Azure Functions) to scale applications dynamically based on demand.
Network Optimization:
- Optimize bandwidth and minimize latency by using optimized routing and direct connections (e.g., AWS Direct Connect).
Exam Tips:
- Focus on auto-scaling, load balancing, and caching for performance.
- Understand right-sizing resources and network optimization.
- Be familiar with serverless architecture for scalability.
14 Multi-Cloud and Hybrid Cloud Management
Link : multi cloud & hybrid cloud

Multi-Cloud and Hybrid Cloud Management are key concepts in modern IT infrastructure and cloud computing. Here's an explanation of these terms, their types, and real-life examples of how they apply:
1. Multi-Cloud Management
Definition:
- Multi-cloud refers to the use of multiple cloud computing services from different providers (e.g., AWS, Google Cloud, Microsoft Azure) to avoid relying on a single vendor.
- Multi-cloud management involves tools and strategies used to orchestrate, monitor, and manage multiple cloud services across different providers seamlessly.
Types of Multi-Cloud:
- Public Multi-Cloud: Involves using multiple public cloud providers for various services. For example, an organization may use AWS for computing, Google Cloud for AI, and Azure for storage.
- Private Multi-Cloud: A combination of private cloud resources and multiple public cloud services. Some business-critical applications may be hosted on private clouds, while non-sensitive services might run on public clouds.
Real-Life Example:
- A company like Netflix uses a multi-cloud strategy where they use AWS for their core streaming infrastructure but also employ Google Cloud for specific machine learning services and Microsoft Azure for analytics and data storage. This ensures redundancy, better performance optimization, and risk diversification.
2. Hybrid Cloud Management
Definition:
- Hybrid Cloud refers to a cloud infrastructure that combines both private and public clouds, enabling data and applications to be shared between them. This provides businesses with greater flexibility and more deployment options.
- Hybrid Cloud Management involves managing both private and public cloud environments in a unified manner, ensuring that data and applications can move seamlessly across clouds and organizations can optimize their cloud use.
Types of Hybrid Cloud:
- Cloud Bursting: Involves transferring workloads from a private cloud to a public cloud during peak demand times.
- Distributed Hybrid Cloud: The private and public clouds are located in different geographic locations, but the organization manages them as one system.
Real-Life Example:
- Volkswagen Group of America uses a hybrid cloud to run their critical operations in a private cloud (ensuring security and privacy for sensitive data) while using a public cloud for running scalable, less sensitive workloads like customer service applications. When demand spikes, the company "bursts" its workloads to the public cloud to handle the additional load.
Key Differences Between Multi-Cloud and Hybrid Cloud:
Cloud Environment:
- Multi-Cloud: Involves multiple clouds from different providers, with each cloud running independently.
- Hybrid Cloud: Combines both private and public clouds, with data and applications able to move across them.
Purpose:
- Multi-Cloud: Used for minimizing reliance on one provider and leveraging the strengths of different cloud services.
- Hybrid Cloud: Used for integrating on-premises infrastructure with cloud environments to maintain flexibility and optimize workloads.
Real-Life Scenarios:
Financial Sector (Multi-Cloud): A global bank may use AWS for processing transactions, Google Cloud for advanced analytics, and Azure for compliance and security-related services. This ensures they have the best-in-class services from different providers while also ensuring redundancy and reducing risks.
Healthcare (Hybrid Cloud): A healthcare provider may use a private cloud to store patient data securely (for compliance with regulations such as HIPAA) while using a public cloud for less sensitive services like appointment scheduling or medical research. This allows for better scalability and cost efficiency without compromising security.
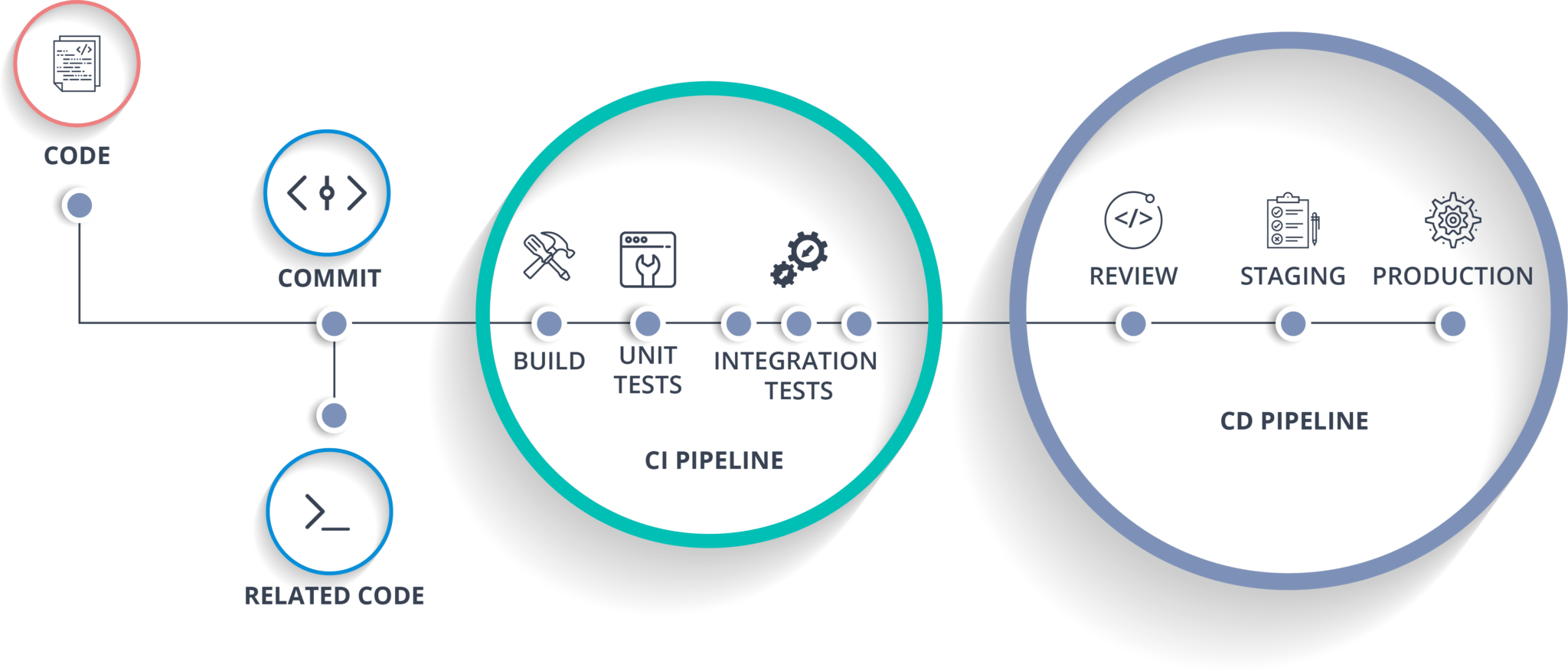
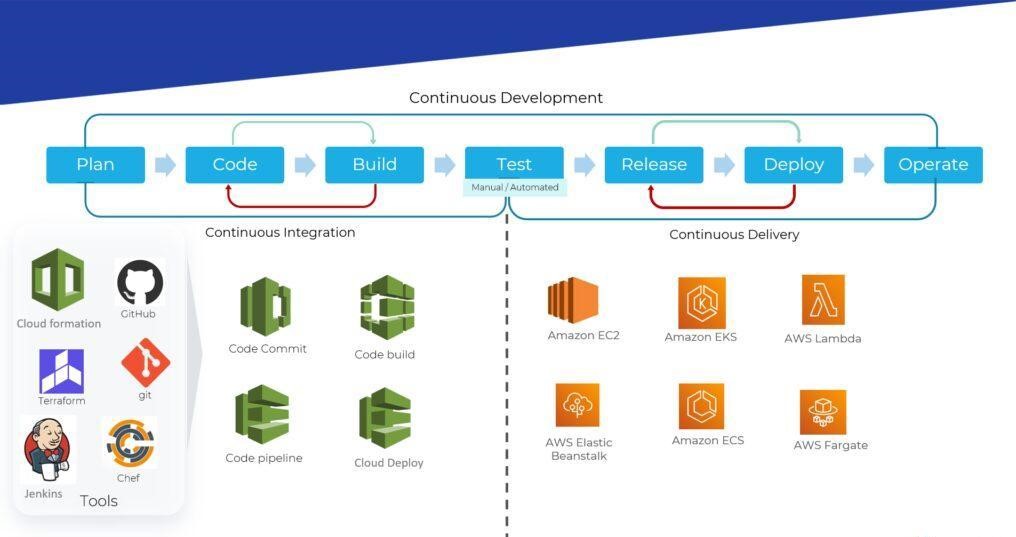
Continuous Integration/Continuous Deployment (CI/CD)
LINK ; CI/CD
Explanation:
CI/CD is a set of practices and tools designed to automate and streamline software development processes.
- Continuous Integration (CI) ensures that developers frequently merge their code changes into a shared repository, where automated tests and builds validate the updates.
- Continuous Deployment (CD) or Continuous Delivery automates the release of software, ensuring new code changes are delivered to production quickly and reliably.
Types:
- Continuous Integration: Frequent code integration and automated testing to ensure code stability.
- Continuous Delivery: Automates the delivery of validated builds to a staging environment for manual approval.
- Continuous Deployment: Fully automates the release process, deploying code changes directly to production.
Advantages:
- Improved Code Quality: Early detection of bugs through automated testing.
- Faster Time-to-Market: Speeds up software delivery.
- Enhanced Collaboration: Encourages frequent commits, promoting teamwork and reducing integration conflicts.
- Scalability: Enables teams to handle larger and more complex projects efficiently.
Limitations:
- Initial Setup Costs: Requires time and resources to implement properly.
- Complexity in Testing: Comprehensive test coverage is challenging for large applications.
- Dependency Management: Ensuring compatibility across tools and frameworks can be difficult.
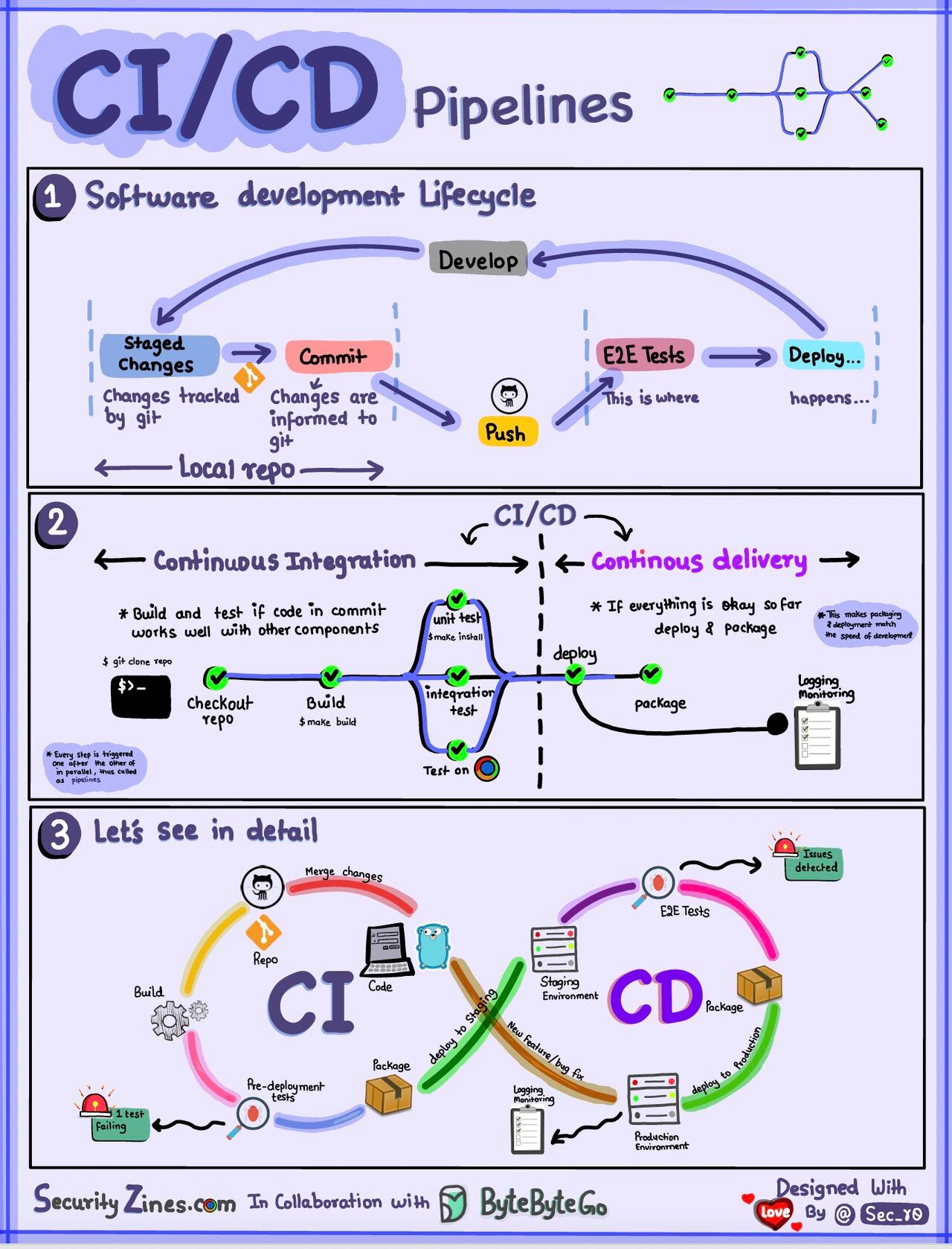
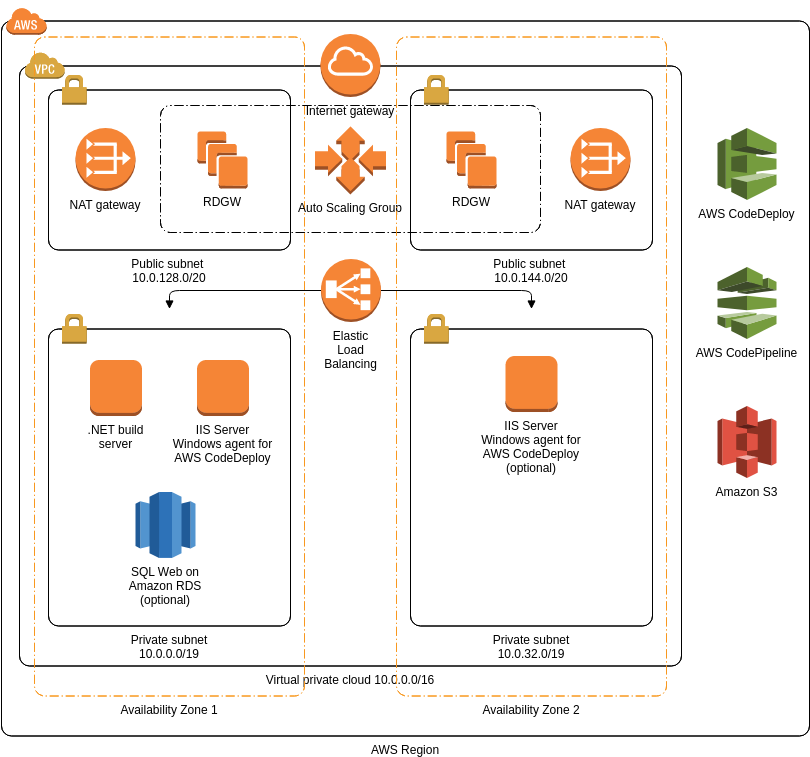
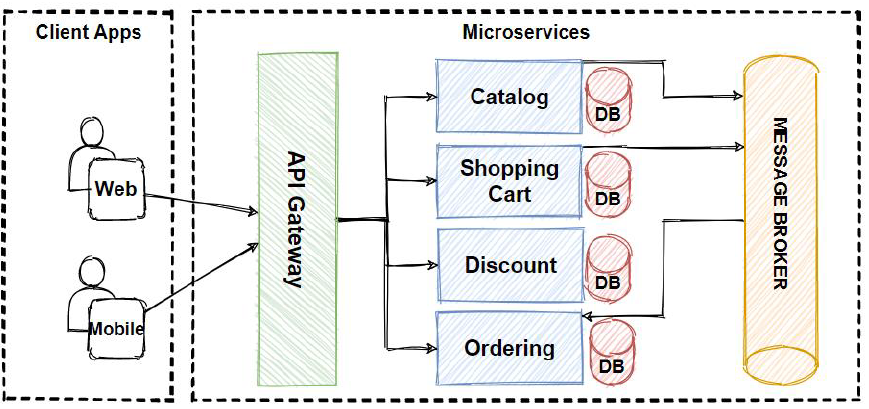
Microservices Architecture
link = microservices-architecture
Explanation:
Microservices architecture is a design approach where a software application is composed of small, independently deployable services that communicate with each other via APIs. Each service is focused on a specific functionality or business capability.
Types:
- Stateless Microservices: No need to store session data; they retrieve required information externally.
- Stateful Microservices: Retain information about the client session or transaction.
- Event-Driven Microservices: Use events to trigger actions and communicate between services.
- Service-Oriented Microservices: Provide specialized functionality, such as logging, monitoring, or authentication.
Advantages:
- Scalability: Services can be scaled independently based on demand.
- Resilience: Failures in one service don’t affect the entire application.
- Flexibility: Different services can use different technologies and languages.
- Faster Development: Teams can work on different services simultaneously.
Limitations:
- Increased Complexity: Managing multiple services introduces overhead.
- Latency Issues: Communication between services may lead to increased response times.
- Deployment Challenges: Requires sophisticated orchestration and monitoring tools.
- Cost Overhead: Increased infrastructure and operational costs due to distributed systems.
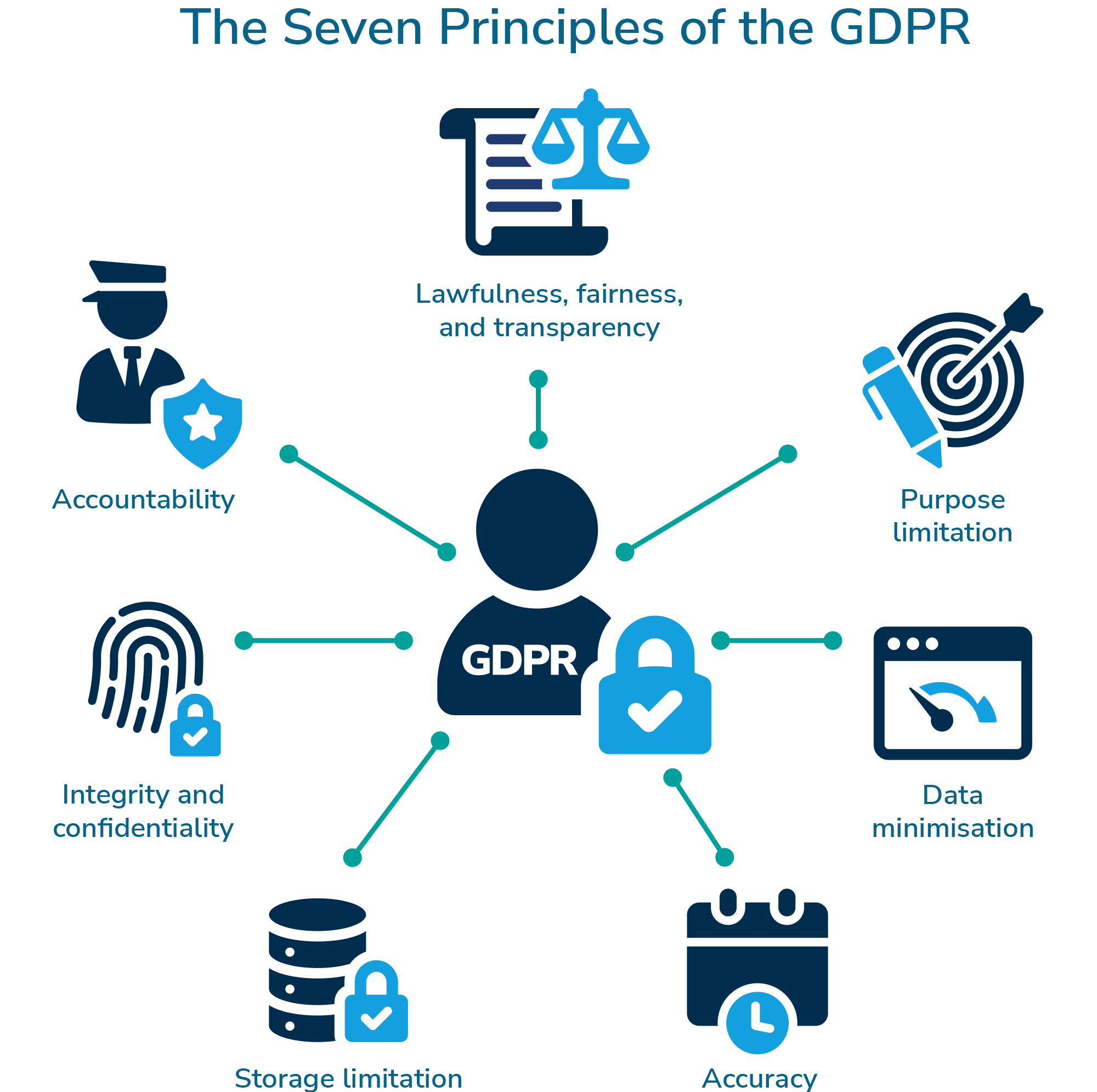
General Data Protection Regulation (GDPR)
Explanation:
The General Data Protection Regulation (GDPR) is a legal framework enacted by the European Union (EU) in 2018. It governs the collection, processing, storage, and protection of personal data of EU citizens, ensuring their privacy rights.
Types of Data Regulated:
- Personal Identifiable Information (PII): Names, addresses, emails, phone numbers, etc.
- Sensitive Data: Health records, biometric data, political opinions, religious beliefs, etc.
- Behavioral Data: Browsing history, IP addresses, location data, etc.
Advantages:
- Enhanced Data Privacy: Provides robust protection for individuals’ personal data.
- Increased Consumer Trust: Encourages transparency and responsible data handling.
- Global Impact: Influences data protection policies worldwide.
- Reduced Data Breaches: Mandates strict security measures.
Limitations:
- Compliance Costs: High cost for businesses to implement GDPR measures.
- Complexity: Strict requirements can be challenging for small organizations.
- Fines: Non-compliance results in significant penalties.
- Global Challenges: Non-EU businesses must navigate international compliance.
Identity and Access Management (IAM)
LINK = HACK IAM
Explanation:
Identity and Access Management (IAM) refers to the framework of policies, technologies, and practices used to manage digital identities and control access to systems, applications, and data.
IAM ensures the right individuals or systems access the right resources at the right times for the right reasons.
Types:
- Single Sign-On (SSO): Allows users to access multiple systems with one set of credentials.
- Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring two or more verification methods.
- Privileged Access Management (PAM): Controls access to critical systems by limiting it to privileged accounts.
- Federated Identity Management: Enables identity linking across different organizations or domains.
Advantages:
- Enhanced Security: Protects against unauthorized access and reduces identity theft risks.
- Improved User Experience: Simplifies login processes with SSO and unified credentials.
- Regulatory Compliance: Supports adherence to regulations like GDPR and HIPAA.
- Scalability: Easily adapts to the needs of growing organizations.
Limitations:
- Implementation Complexity: Requires careful planning and resources to set up effectively.
- System Interdependencies: IAM solutions often depend on other systems being secure.
- Cost: Advanced IAM tools can be expensive for small businesses.
- User Resistance: Users may resist MFA or SSO due to perceived inconvenience.
Conclusion:
As businesses continue to evolve in the digital age, adopting flexible, scalable, and resilient cloud strategies is no longer optional—it's essential. Multi-cloud and Hybrid cloud management offer powerful solutions for companies seeking to optimize their cloud usage, reduce risks, and enhance performance. By using multiple cloud providers or combining private and public clouds, businesses can ensure they are not tied to a single vendor, maintain control over their sensitive data, and scale their operations seamlessly.
These cloud strategies provide greater agility, better resource optimization, and the ability to meet the dynamic needs of modern enterprises. Whether you're looking to avoid vendor lock-in with multi-cloud or ensure flexibility and security with a hybrid approach, embracing these solutions will position your organization for continued growth and success in an increasingly cloud-driven world.
Incorporating multi-cloud and hybrid cloud management into your business strategy is an investment in future-proofing your infrastructure and maintaining a competitive edge in today’s fast-paced, technology-driven landscape. The future of cloud computing is diverse and adaptable—are you ready to take advantage of it?













Comments
Post a Comment